- Hack Forums: Emphasis on white hat, with categories for hacking, coding and computer security.
- SecurityFocus: Provides security information to all members of the security community, from end users, security hobbyists and network administrators to security consultants, IT Managers, CIOs and CSOs.
- Exploit DB: An archive of exploits and vulnerable software by Offensive Security. The site collects exploits from submissions and mailing lists and concentrates them in a single database.
- SecTools.Org: List of 75 security tools based on a 2003 vote by hackers.
- The Hacker News: The Hacker News — most trusted and widely-acknowledged online cyber security news magazine with in-depth technical coverage for cybersecurity.
- Hacked Gadgets: A resource for DIY project documentation as well as general gadget and technology news.
- Offensive Security Training: Developers of Kali Linux and Exploit DB, and the creators of the Metasploit Unleashed and Penetration Testing with Kali Linux course.
- KitPloit: Leading source of Security Tools, Hacking Tools, CyberSecurity and Network Security.
- DEFCON: Information about the largest annual hacker convention in the US, including past speeches, video, archives, and updates on the next upcoming show as well as links and other details.
- Packet Storm: Information Security Services, News, Files, Tools, Exploits, Advisories and Whitepapers.
- HackRead: HackRead is a News Platform that centers on InfoSec, Cyber Crime, Privacy, Surveillance, and Hacking News with full-scale reviews on Social Media Platforms.
- Black Hat: The Black Hat Briefings have become the biggest and the most important security conference series in the world by sticking to our core value: serving the information security community by delivering timely, actionable security information in a friendly, vendor-neutral environment.
- NFOHump: Offers up-to-date .NFO files and reviews on the latest pirate software releases.
- Phrack Magazine: Digital hacking magazine.
- Metasploit: Find security issues, verify vulnerability mitigations & manage security assessments with Metasploit. Get the worlds best penetration testing software now.
- Hakin9: E-magazine offering in-depth looks at both attack and defense techniques and concentrates on difficult technical issues.
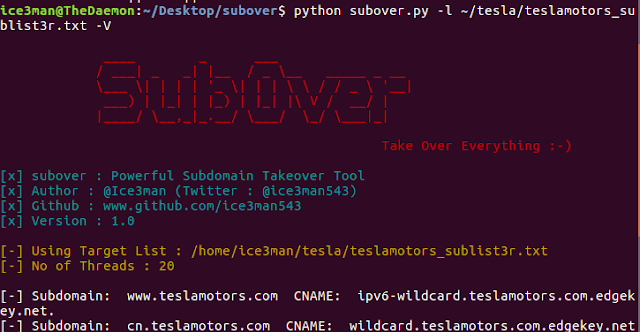
Subover is a Hostile Subdomain Takeover tool designed in Python. From start, it has been aimed with speed and efficiency in mind. Till date, SubOver detects 36 services which is much more than any other tool out there. The tool is multithreaded and hence delivers good speed. It can easily detect and report potential subdomain takeovers that exist. The list of potentially hijackable services is very comprehensive and it is what makes this tool so powerful.
Installing
You need to have Python 2.7 installed on your machine. The following additional requirements are required -
- dnspython
- colorama
git clone https://github.com/Ice3man543/SubOver.git .
cd SubOver
# consider installing virtualenv
pip install -r requirements.txt
python subover.py -hUsage
python subover.py -l subdomains.txt -o output_takeovers.txt-l subdomains.txtis the list of target subdomains. These can be discovered using various tool such as sublist3r or others.-o output_takeovers.txtis the name of the output file. (Optional & Currently not very well formatted)-t20 is the default number of threads that SubOver will use. (Optional)-Vis the switch for showing verbose output. (Optional, Default=False)
Currently Checked Services
- Github
- Heroku
- Unbounce
- Tumblr
- Shopify
- Instapage
- Desk
- Tictail
- Campaignmonitor
- Cargocollective
- Statuspage
- Amazonaws
- Cloudfront
- Bitbucket
- Squarespace
- Smartling
- Acquia
- Fastly
- Pantheon
- Zendesk
- Uservoice
- WPEngine
- Ghost
- Freshdesk
- Pingdom
- Tilda
- Wordpress
- Teamwork
- Helpjuice
- Helpscout
- Cargo
- Feedpress
- Freshdesk
- Surge
- Surveygizmo
- Mashery
FAQ
Q: What should my wordlist look like?
A: Your wordlist should include a list of subdomains you're checking and should look something like:
backend.example.com
something.someone.com
apo-setup.fxc.something.comYour tool sucks!
Yes, you're probably correct. Feel free to:
- Not use it.
- Show me how to do it better.
Contact
Twitter: @Ice3man543
Credits
- Subdomain Takeover Scanner by 0x94
- subjack : Hostile Subdomain Takeover Tool Written In GO
- Anshumanbh : tko-subs